The fake coupon scam gained traction in 2016 and is still tricking consumers to this day. It becomes even more prominent around back-to-school, Thanksgiving, Mother’s Day, Black Friday, and Christmas.
These bogus coupons claim to be from well-known companies such as Target, Starbucks, Whole Foods, Food Lion, Kroger, Aldi, Lowe’s, Dunkin Donuts, Kohl’s, Publix, Dollar General, and Bed Bath and Beyond. The coupons often claim to be in celebration of the company’s anniversary or birthday. Some of the offers that have been used in the past, include:
- Free $30 gift card
- 50 percent off store wide
- $75 off any purchase
- $50, $100, and $200 off
Usually “all you have to do” to get the coupon is like the page, share the coupon with your friends, and fill out a survey.
Once you click on the fake coupon, a couple of things may happen:
You’re taken to a bogus website asking for personal information such as your name, phone number, age, email, and home address. You’ll find yourself completing survey after survey and never actually getting the coupon. Scammers often get paid for every completed survey, so it’s possible that they phish enough information out of you to retrieve passwords and access your accounts. Best case scenario, you just get bombarded with spam emails.
Worst case scenario, you’re taken to some website you’ve never head of and that site starts installing malware on your computer.
If at any point, you’re told to download an app or software to get the coupon, DON’T do it. It’s a scam.
My Experience
If I’m being completely honest, I fell victim to this very scam a few years ago. I saw several of my friends share an awesome Target coupon and figured if they posted it, it must be fine. I don’t remember the exact details, but I know it took me to a website where it asked me to fill out a survey. I completed the survey, only to have it redirect me to another survey. I really wanted that coupon, so I took a few more surveys before finally giving up. Next thing I know, I’m getting messages from friends telling me that my Facebook account was hacked. I went through my account activity and saw that hackers posted in groups and commented as me. It probably would have taken me weeks (or longer) to discover my account was compromised if my friends didn’t tell me. I immediately changed my password and started unsubscribing from the dozens of spam emails in my inbox.
Lessons Learned
Anything that seems too good to be true, almost always is.
Businesses do not celebrate anniversaries by giving away hefty coupons to Facebook users who like and share posts.
You know better. Nothing is ever free. Most companies can not afford to give out $200 to every person who likes their Facebook post. And when was the last time Starbucks handed out $100 gift cards like candy? That’s what their reward program is for.
How to Spot a Fake Coupon
Check to see if the Facebook page is legitimate.
The Facebook page may look real. Scammers often steal logos and photos from the official page. Check to see if the page is verified (it’ll have a blue or grey circle with a check mark next to the name).
Scammers will change the name of the Facebook page slightly. The official Facebook page may be called Aldi USA and the fake one may be called Aldi US. They also might use a page called “Aldi coupons” or “Aldi Deals”
Not every company has a verified Facebook page. If you’re unsure if the page is official, go to the company’s website and look for their Facebook information there. You can also contact them directly to verify the name of their page or simply ask about the coupon.
Pay close attention to the link destination, before even thinking about clicking on it.
If the URL is Target.com-holidays.xyz it’s a scam. Make sure the link goes to the official company website BEFORE clicking on it.
Check for fine print.
All legitimate coupons have fine print containing terms and conditions, exceptions to the sale, and an expiration date.
You’re required to fill out a survey, like or share.
I looked at Facebook pages for several of the companies that are often targeted in this scam (Kohl’s, Target, and Starbucks) to find legitimate coupons for comparison. Out of the three companies, not one of them posted an actual coupon. They gave information about sales and deals, links to deals on their websites, and information about in-store freebies. Not once, did they ask you to share, follow, like, or fill out a survey to access the deal, offer, or in-store freebie. Note: things are slightly different regarding social media contests and giveaways. However, as far as coupons go, you will NEVER need to give out personal information or like and share a post.
Check for low resolution or grainy images.
If you’re still unsure of the legitimacy of a coupon, check out Snopes.com or the BBB scam tracker. Even better, contact the company directly to inquire about the coupon.
What to Do If You Spot a Fake Coupon
Report it to the retailer mentioned so they handle it as they see fit (press release, warn customers, try to get it removed from social media, etc.)
Don’t share it or click on it.
If you see that your friends already shared it, tell them to change their passwords.
Report it to Facebook.
Examples

This FAKE Dollar General coupon was circulating Facebook in June 2018. A real coupon would have more fine print. Also, take note of the odd capitalization and mistakes. Why is “Providing” capitalized? 80th years? SCAM! Yet it was still shared by thousands of people.
The Starbucks gift card scam has been around since at least 2011 and it’s still fooling people today. This screenshot was taken from a post I saw on my feed yesterday. Look at the URL. It doesn’t go to the official Starbucks website. It goes to Starbucks.Happyhour.Cards. Pay attention to URL destinations!
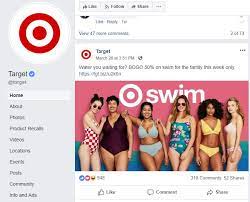
First, notice how there is a check mark next to the company name. That means it’s a verified company. Next, you’ll notice it’s not an actual coupon. It’s a link to their website so you can shop the deal. Anyone can access the deal without liking, sharing, or filling out a survey.
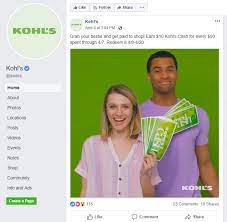
You’ll notice the check mark next to the company name. Again, it’s not an actual coupon. It just mentions an offer. It touches on some of the terms and conditions (when you can earn it and when you can redeem it). Finally, it never asks for any personal information. You don’t have to fill out a survey or like or share anything to earn the Kohl’s cash.