Online shopping is blowing up the internet, now more than ever before, and we all know why! This pandemic has crippled the traditional shopping trends, and now Cyber Monday may be the biggest sale of the year.
Not only do major retailers put their items on sale, but individual retailers and secondhand shops will also most likely have their deals as well.
The Facebook marketplace has grown in considerable popularity in the last couple of years as a substantially accessible pathway for individuals to sell their used or specialty goods.
Buying items through Facebook is often very affordable and accessible when the seller is local. But sadly, like every other enjoyable experience in life, there have been those who take others’ vulnerability to their advantage to make a profit.
Don’t Purchase or Sell Through Any Online Platform Until You Know These 3 Things:
- Make sure the seller or buyer is credible, and they are correctly using the platform (Facebook Marketplace has their messaging system to keep track of transactions and conversations. If they message you outside of this system, it is an instant RED FLAG)
- The payment method they would like to use is not popular or is not lining up with PayPal or Venmo’s policy (see below to read more about how Paypal is getting compromised).
- They overpay you, or the seller wants too little for the product; this is often one of the biggest mistakes the scammers make!
What is Paypal Scam on Facebook?
A PayPal scam on Facebook is a type of online scam that uses the popular payment platform PayPal to trick unsuspecting users into sending money or personal information to the scammer. The scam typically begins with a message from the scammer, who may pose as a friend or family member, asking for money for an emergency or other reason. The scammer may also send a link to a fraudulent website that looks like the real PayPal website. If the user clicks on the link, they will be asked to enter their personal information, such as their credit card number or bank account information. The scammer will then use this information to steal the user’s money or identity.
There are a few things you can do to protect yourself from PayPal scams on Facebook:
Only accept friend requests from people you know in real life.
Be wary of any message or request from a stranger who claims to need money for an emergency.
Never click on links in messages from people you don’t know.
If you’re unsure whether a website is legitimate, look for the “https://” in the URL and make sure the website is secure.
Never enter your personal information on a website that you don’t trust.
If you think you may have been scammed, you should report it to PayPal and your bank immediately. You should also change your passwords and monitor your accounts for any suspicious activity.
Here are some examples of PayPal scams on Facebook:
The scammer sends a message to a user claiming to be from PayPal. The message says that the user’s account has been suspended and that they need to provide their personal information, such as their credit card number or bank account information, to verify their identity.
The scammer sends a link to a fraudulent website that looks like the real PayPal website. If the user clicks on the link, they will be asked to enter their personal information. The scammer will then use this information to steal the user’s money or identity.
The scammer creates a fake PayPal account that looks like the real PayPal account. The scammer then sends a message to a user asking them to send money to the fake account.
If you receive a message or link from someone you don’t know, be very careful before clicking on it or providing any personal information. If you’re unsure whether something is legitimate, it’s always best to err on the side of caution and not click on anything or provide any information.
How Does facebook Marketplace Scam Works?
Facebook Marketplace is a popular online marketplace where people can buy and sell items. However, it is also a popular platform for scammers to operate. There are a number of different scams that can occur on Facebook Marketplace, but some of the most common include:
Fake listings: Scammers will create fake listings for items that are in high demand, such as electronics or furniture. The listings will often be priced below market value to attract buyers. Once a buyer expresses interest, the scammer will ask them to pay for the item through a wire transfer or other untraceable payment method. The scammer will then disappear with the money and never deliver the item.
Overpayment scams: Scammers will offer to pay more than the asking price for an item. Once the buyer agrees to sell the item, the scammer will send a fake check or money order. The check or money order will initially appear to clear, but it will eventually bounce. When this happens, the buyer will be out the item and the money they sent to the scammer.
Shipping scams: Scammers will ask buyers to ship items to them before they have paid for them. Once the buyer ships the item, the scammer will disappear with the item and never pay for it.
Fake profiles: Scammers will create fake profiles that look like real people. They will then use these profiles to contact buyers and sellers and try to scam them out of money.
There are a few things you can do to protect yourself from scams on Facebook Marketplace:
Only buy from people you know and trust: If you don’t know the person you’re buying from, do some research on them before you make a purchase. You can look at their profile to see if they have any reviews or if they’ve been involved in any scams in the past.
Never pay for an item before you see it in person: This is especially important for high-value items. If you can’t see the item in person, there’s a good chance you’re being scammed
Meet in a public place: When you meet to buy or sell an item, do it in a public place where there are other people around. This will help to deter scammers and make it easier for you to get help if something goes wrong.
Use a secure payment method: When you pay for an item, use a secure payment method like PayPal or a credit card. This will give you some protection if you’re scammed.
If you think you may have been scammed on Facebook Marketplace, you should report it to Facebook. You should also contact your bank or credit card company and file a fraud report.
How can you spot a Paypal scammer on Facebook?
Here are some tips on how to spot a PayPal scammer on Facebook:
Be wary of any message or request from a stranger who claims to need money for an emergency. Scammers often pose as friends or family members in need of help. If you receive a message from someone you don’t know asking for money, be very careful before sending anything.
Never click on links in messages from people you don’t know. Scammers often use links to fraudulent websites that look like the real PayPal website. If you click on a link and enter your personal information, the scammer can steal your money or identity.
If you’re unsure whether a website is legitimate, look for the “https://” in the URL and make sure the website is secure. The “https://” indicates that the website is secure and that your information is protected.
Never enter your personal information on a website that you don’t trust. This includes your credit card number, bank account number, or Social Security number.
If you think you may have been scammed, report it to PayPal and your bank immediately. You should also change your passwords and monitor your accounts for any suspicious activity.
Here are some examples of PayPal scams on Facebook:
The scammer sends a message to a user claiming to be from PayPal. The message says that the user’s account has been suspended and that they need to provide their personal information, such as their credit card number or bank account information, to verify their identity.
The scammer sends a link to a fraudulent website that looks like the real PayPal website. If the user clicks on the link, they will be asked to enter their personal information. The scammer will then use this information to steal the user’s money or identity.
The scammer creates a fake PayPal account that looks like the real PayPal account. The scammer then sends a message to a user asking them to send money to the fake account.
If you receive a message or link from someone you don’t know, be very careful before clicking on it or providing any personal information. If you’re unsure whether something is legitimate, it’s always best to err on the side of caution and not click on anything or provide any information.
How can you protect yourself from Paypal Scams on Facebook?
Here are some tips on how to protect yourself from PayPal scams on Facebook:
Only accept friend requests from people you know in real life.
Be wary of any message or request from a stranger who claims to need money for an emergency. Scammers often pose as friends or family members in need of help. If you receive a message from someone you don’t know asking for money, be very careful before sending anything.
Never click on links in messages from people you don’t know. Scammers often use links to fraudulent websites that look like the real PayPal website. If you click on a link and enter your personal information, the scammer can steal your money or identity.
If you’re unsure whether a website is legitimate, look for the “https://” in the URL and make sure the website is secure. The “https://” indicates that the website is secure and that your information is protected.
Never enter your personal information on a website that you don’t trust. This includes your credit card number, bank account number, or Social Security number.
If you think you may have been scammed, report it to PayPal and your bank immediately. You should also change your passwords and monitor your accounts for any suspicious activity.
Here are some additional tips to help you protect yourself from PayPal scams on Facebook:
Keep your software up to date. Software updates often include security patches that can help protect you from scams.
Use a strong password for your PayPal account. Your password should be at least 8 characters long and include a mix of letters, numbers, and symbols.
Enable two-factor authentication for your PayPal account. Two-factor authentication adds an extra layer of security by requiring you to enter a code from your phone in addition to your password when logging in.
Be aware of the latest scams. Scammers are constantly coming up with new ways to steal money from people. It’s important to stay informed about the latest scams so you can avoid them.
By following these tips, you can help protect yourself from PayPal scams on Facebook.
More About The Paypal Scam:
Paying through Paypal is one of the most reliable forms of online payment there is. They are incredibly secure, but the hackers use a very well-formatted email that looks like it’s coming from PayPal. The Hacker’s goal in this example is to get your product without paying for it.
When you pay with PayPal, you can easily find the recipient by looking up the shipper’s email. The hackers use this to their advantage, asking for your email and name on the account. They then compose an email that appears to be sent by PayPal. However, it doesn’t appear in your app until the product has shipped, and there is proof of shipment.
Look carefully at the sender information in this email. It says it’s from Paypal.com, but look again; it is actually from Shipmenttrackingproof@post.com, which is not affiliated with PayPal at all. A legitimate payment will always send emails from service@paypal.com.
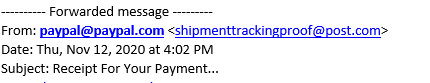
Now let us look at the full body of the email:
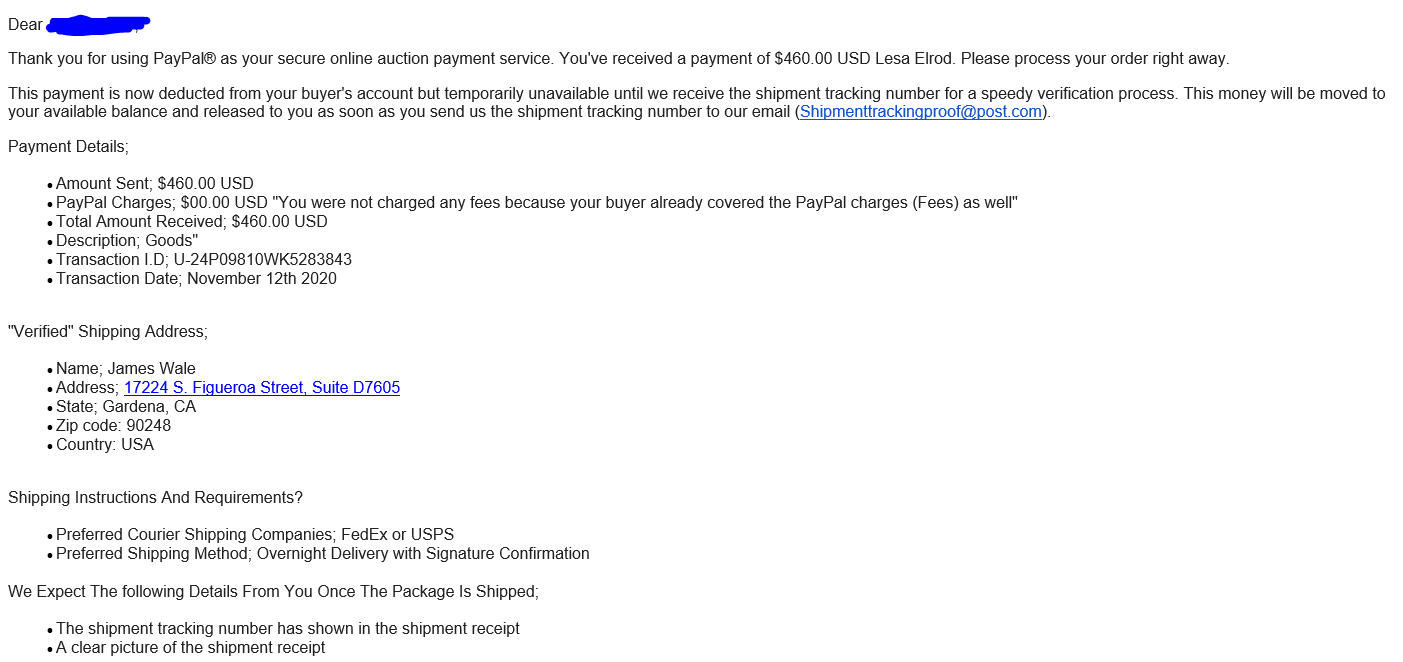
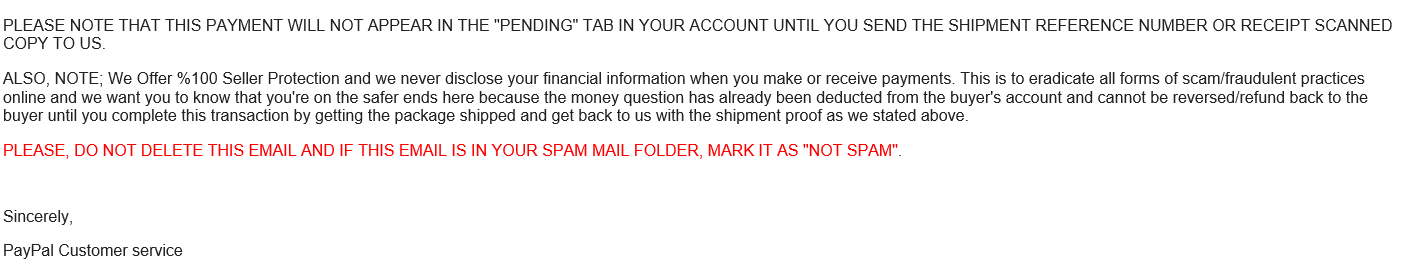
This seller would have paid the shipping cost for the scammer to steal the item! Now that is adding an insult to injury!
While the scammers may have pulled this email template from a legitimate email that PayPal uses, always check the three warning signs listed above before purchasing anything online.
Have you been compromised? Contact Computerbilities for a Free no Obligation Dark Web Scan!
https://www.computerbilities.com/dark-web-scan/